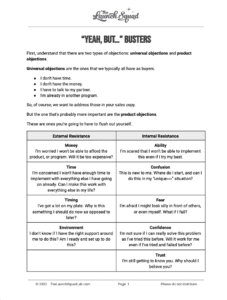
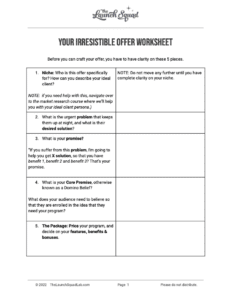
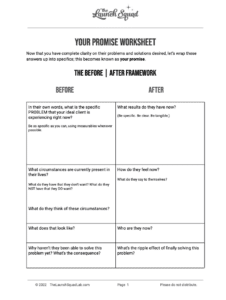
Think hackers don’t care about you and your little ol’ business? Think again!
Phishing, vishing, smishing, spear phishing, whaling, ransomware…
Why do these words sound like sailor jargon out of Moby Dick? Because the internet’s a stormy sea, mate, and these hackers are the pirates trying to board your web-ship and take what’s yours. It’s enough to make you say, argh!!!
Luckily, The Launch Squad has your back, and we’re going to keep reminding you to get a Password Manager until we’re as blue as the sea!!
Also, learn the 5 important things you need to do to feel safe online.
Katie: Welcome to the light in your launch podcast today, we're talking about cybersecurity and why you as a small business are their biggest target. Stay tuned.
Announcer: Hey, we're in the Launch Squad and this is the Light Your Launch podcast. We teach coaches and course creators how to lighten their launches. We're bringing you all of the tips and strategies to take your launch from intimidating to money-making. In this podcast, we talk about everything; the sales, strategy, mindset, technical and spiritual aspects of running your best launch ever. So if you're feeling overwhelmed and unsure of the next right step, we're here to bring clarity, confidence, and excitement into your next launch. This is the Light Your Launch podcast. [inaudible]
Katie: Welcome back to the show. I'm Katie Collins, speaking with Jeffrey, and today we want to talk to you about cyber security. So this is definitely Jeffrey's topic. And I know we're all in agreement that internet security and hacking in particular is a hot topic, but why do smaller businesses need to pay extra close attention to this topic right now?
Jeffrey: I am glad you asked that question and this is something that I hear a lot. And here's the thing. If, if you're out there in listening world, if you are our, uh, our one podcast listener and, um, you've asked yourself this question, like, why would an attacker want to attack me? I have like, I don't do e-commerce or maybe I do, but I'm such small, small fish. Like why would, why would anybody want to attack me? So if you've been asking yourself that if you've ever thought that this is an episode for you, so here are some sobering statistics, uh, that sort of hit this nail on the head. 71% of attacks are against businesses under a hundred employees. AKA that's your business basically. Yeah. Right. Small businesses are actually the number one target for attacks. And 82% of small business owners believe they're safe because they have nothing of value. Now, just during this pandemic, the FBI has reported a 300% increase in cyber attacks and wow. Those are all against us. The small business, right? 71%. How crazy is that?
Katie: Yeah. Yeah. I had a friend that worked security for a big firm and he shared some of that same stuff and I was the person that was like, I don't want to have to remember all these different passwords meet, meet me. And he would just be like, it's people just like you, that named their password after their dog that got hacked the most.
Jeffrey: Yep. Yep.
Katie: Yeah. So, um, so he did help me understand, um, you know yeah. What, what, why it's so important. Um, so what do you suggest, you know, we do kind of as these small people that don't have a chief technology officer,
Jeffrey: Right?
Katie: How, you know, how do you suggest that we approach security when it comes to our small businesses?
Jeffrey: So there's basically five steps to this whole thing and we'll focus on just a couple of them, but you've got to identify, protect, detect, respond, and recover, responding and recover. That's kind of obvious, right? If something's wrong, you're going to respond to it and you're going to get it fixed. Right. So identifying, protecting, and detecting. Those are the three things. The three areas where people are like, well, what do we do? And how do we proactively do that? And you know, things like that. And so, um, really when it comes to identifying, you're looking at what your weakest link is like, knowing what devices you do business on, where, what websites you do business on what software you do business on what devices you do business on. Basically you're identifying what are the ways in which someone might attack me. That's your laptop, desktop phone, whatever. Right. It's your, uh, okay,
Katie: Good. I was going to interrupt you and be like back it up, back it up. Yes. Let's pretend that I'm five.
Jeffrey: I do that all the time anyway.
Katie: Because in tech speak I'm about I'm about there. Um, no, but really so understanding that your phone can get hacked, your tablet can, what about like your smart TV or people have like Alexa in their home, things like that. I don't trust that kind of stuff, but are can, all of those also get hacked?
Jeffrey: They can. And oftentimes things like Alexa have less to do with our business, but sometimes more to do with our homes. Um, there's been videos of people hacking, uh, smart locks, you know, so you can use Alexa through, uh, somebody I'm blanking on the actual test, but it was like somebody used a laser to send a signal to Alexa that unlock the doors. Like somebody can just literally go up to your, your house peer in your windows, see that you have Alexa point of laser at it, send a certain signal and your front door unlocks. Wow. Right. Yeah. Crazy stuff.
Katie: So, yeah. So it's like it can happen in the personal life. And I think, I think where my head went with that was if they get, you know, a password that you have Alexa, Amazon related, how many of you might use that same password in business stuff. So, you know, if they can hack into your computer and then look at your history and see the sites you go to and try that password, um, you know, it can become a big, a big hornet's nest for sure.
Jeffrey: Yeah. And what you're touching on there is actually the weakest point of security that I think we should spend some time here and talk about, like, if we had to do one, if we had to do one and focus on one area of security, what would that be? And it's your password. It really is. Here's, here's a sobering statistic also, no matter how many, um, special characters you use, it'll take somebody eight hours with a normal computer to brute force that password, uh, sorry, an eight character password, eight hours for an eight character password. Like eight characters is a lot. And that's like sometimes more than a birthday date, things like that, you know? Um, right. And here here's where the two, two things about this really matter the length of the password. Um, uh, by the way, a five digit is instantaneous. It takes a normal computer less than one second to crack that. Okay. So if you're using five digits yeah. If you're using five digits, you're instantly hackable instantly.
Katie: And you notice that, you know, when you start, um, these sites are getting more and more, um, what's the word I want. Um, sophisticated. And so now it's, you know, it's going to have an uppercase and lowercase and a numeric key and a special key and you know, it cannot be blah-blah-blah right. So very sophisticated. So they almost don't let you have those five digit passwords anymore because they know how easily hackable it is. So, yeah,
Jeffrey: You'll, you'll notice that a lot of bank, uh, bank companies or bank websites will say between eight and 12, is there, is there requirement. And what's weird that I don't like is that you can't, you can't make it 13 or 14 or more, but I think they're trying to mitigate the amount of people who will forget what their password is. Right. So 12 characters is like the maximum, and here's the thing that, that threshold, there's a time what's called a, a time to crack in a year, uh, or tough time to crack. Right. So it's five characters, instant, eight characters, eight hours. And I think 12 characters. Where was, where is, is that certain point where it becomes, um, I dunno, it's like 34,000 years or something like that. Right. It starts to tip. Yeah. And it goes up really quick, really, really quick from eight hours to like 24 years. And then from 24 years to like 34,000 years, you know, something like that where it's like, it is really exponential. So if you think about it, eight characters, I can hack it today, nine characters I could spend, you know, a couple of years and hack your code, 11 characters. I can do it within my lifetime, 12 characters. And it's it's generations of computing. Right. So it really does go up exponentially. And it is the length that co that has the biggest factor.
Katie: Hmm. Now does it have to be like, I got into a habit for a while of, of having my passwords have something to do with a goal, like a money goal that I had, or like one year I was reading think and grow rich. And so my password had a combination that reminded me of that book. Like thinking grow rich in 2020, I didn't spell all those words out, but you get it. Um, you know, so does it matter if it's, if it's like an actual word or is it better if it's one of those random password generators, PQ three to, you know, exclamation Mark, yada yada like a VIN number?
Jeffrey: Well, here's the thing. It, that is important. But again, the length is what's most important because there is, um, because we've had a lot of breaches, I won't say a lot. There's been a few really key breaches where a lot of people's information has been out there. As soon as those breaches happen, those attackers have essentially a list of username and passwords. So now those passwords get upended to this master black hat password list, and anyone who is trying to attack you will go first, go through that list. And literally in less than a second, you know, you know, I don't know how many billions of, uh, known password it can go through in a second, but it goes through that list first. So that's where real words are easier to hack, um, names, places, dates, you know, those things are basically on the standard procedure list for an attacker. So they're going to try those first, if you think your particular word and word combination is something, no one would use chances are you're wrong. Right?
Katie: So like that weakest point, right? Like, well, it's like the weakest point sounds like it's human, it's human, human error. Right? It's like the refusal, like I just started using a password, like an online password management system, um, probably a year, maybe 18 months ago, probably a year. And before that you are going to laugh because we're on video for our listeners. So I know that only Jeffrey can see this on the video, but I'm going to show you my system
Jeffrey: And to let our listeners know she's holding up a handwritten note pad with everything written out. Imagine if she left that on a park bench
Katie: And, and crossed off, right. I crossed off or, well, I didn't have my logins. It's just my passwords. Cause I knew what my logins were, but if I had to update it, I would get out my notebook and cross it off. You know? So this is very 2002. Um, and then I would take a picture of it so that it was in a photo on my phone. So if I were traveling, I could access it. Um, but again, if somebody has my phone, my right, so I totally knew that was dumb. And so as I started getting more and more passwords from my business, I was like, all right, Katie, time to be an adult. Right. And organize it a little bit better. And I would say, my system works well, 90% of the time, it's certainly not flawless. It can be a pain. Um, but for 90% of the time it does work and I'm grateful for it.
Katie: And then it will also generate those stronger passwords for me. And so I just don't have to think about it because they say you never want to repeat the same password for any site. And that's still something that I still have bad habits with. So anyway, I I've grown up and Jeffrey and I, um, you know, I use last pass and Jeffrey uses what one, one password. And we argue weekly on whose is better. Maybe we'll do a whole episode. Right. Who, who do you think knows better Jeffrey or Katie? I would listen to Jeffrey, but let's talk about, you know, what are the types of attacks because I've only heard of phishing with a pH and you know, then when you were telling me about vishing and wailing and smishing, I'm like, are these mate, did you make these up? So what, what are these, what are these different types of, why are they differentiated? Like what do we need to know about these so that I don't want to scare our audience, but I want them to understand and just have more awareness about it.
Jeffrey: Well, I think they will be scared cause I was scared too. Um, and we should all be a scared because this is a real thing and there's some costs to this and we'll get into that, but, okay. So, so there's phishing, vishing whaling, smishing, spear, phishing, and Ransomware, all kinds
Jeffrey: Of the "ishings", right? We've all heard of fishing at this point. And you know, that that's carefully targeted digital messages, such as emails, uh, that are transmitted to fool people into clicking a link that can install malware or expose sensitive data. That's the most, most common attack. Um, now vishing is same thing, but w using, uh, voice phishing, uh, in a, in a phone call or something like if you've ever gotten a call, says, Hey, we're the IRS. Uh, you owe us money. You send us a check, all that kind of stuff. Um, you know, that's, vishing smishing is, I don't know why it's smash, but it's text messaging. Uh, so if you've received a text message that tries to get you to click a link or something like that, uh, now spear fishing,
Katie: Someone at the New York times was like, let's call this smishing. That makes total sense. You know, like I get like vishing is voice with, with fishing, right. But smishing is like, I maybe called it like texting, texting texts. Anyway, sorry to interrupt smishing. Tell us about some, Oh, smishing was the text messaging. All right. What's wailing
Jeffrey: Text meshing. Well, I'll get to whaling. But to, in order to get to whaling, we got to hear what spear fishing is. Spear fishing takes email fishing one step further and typically contains personal information about an individual. Now this is where fishing and whaling kind of coming together. And what this really means is that, um, so for example, someone can go to your social media. Someone could research where you work, someone can research what you're working on. Someone can research where you've been and who you hang out with and where you go shopping. Right? So now they approach fishing from a place of, I know this about you. I know this about you. I know this about you. I know this about you, and it looks like a completely legitimate email. Like I hope you enjoy. I hope you love the dress you just bought at Nordstrom's last week.
Jeffrey: If you're looking for something else, click here for something or whatever, right. Or something where they have personal information about you and they use it in the phishing email. So it's no longer, Hey, we're just kind of some generic thing. We're the IRS. And should click this link. It's way more personal. And then whaling is where they use spear fishing. It's an advance. It's more advanced than spear fishing. And it's designed to gain access to higher profile targets like CEOs and CFOs. Um, those are usually the end targets, uh, but regular employees are used to get to them, right? So this is really kind of more in the corporate world where you have a lot of employees and there's a few people at the top, right. And that's where they would research a worker, you know, look at what they've been doing, where they've been shopping and what, and stuff like that.
Jeffrey: Send them an email that once they click that link, you know, whatever the attack happens, uh, maybe that just lets them into the system and can, they can peruse around the, uh, peruse around the servers or whatever, or maybe it's something else. And maybe it's ransomware. And this is the final one and kind of the, the big kahuna of, of all of the attacks and what sometimes all of these attacks eventually lead to. And what ransomware is, it's any ma malware that holds your data ransom. Um, these days it usually involves encrypting a victim's data before asking for cash, typically cryptocurrency. So this is where something, you know, something pops up and it says, Hey, you just won a $50 Amazon gift certificate, click here to redeem your prize. As soon as you click it, boom, sucker your system is locked down, please deliver $50,000 worth of cryptocurrency to this bank account.
Katie: Yeah, I see that on TV. Um, and it's real. Yeah. So the friend I mentioned earlier that is the chief technology officer of his company. Um, he was not the chief technology officer, but the person who was lost his job, because this exact thing happened and they were held at ransom for like $350,000. Jeez. And my friend got promoted and got them out of that and then has transferred the whole system. And so that's why he was like, it's people like you, that ruin it. You know? And I was like, well, I'm not dumb enough to click on a link in an email, you know, like I'm like, but you know, they are very sophisticated. So I don't mean to say dumb enough because really it's a very sophisticated system and yeah, like very smart people were caught by it because they're just getting smarter and smarter. It's not all these people in Nigeria, it's people that live on your street and they, you know, their grammar and spelling are accurate and everything looks legit. And yeah, so it's certainly not a stupid thing. And that's what I'm really learning. You know, that this is a very real, real thing. And, you know, I had that question to you when we talked about getting, um, Google drive file stream. What's it called now?
Jeffrey: Google, Google drive for desktop or something. Yeah.
Katie: Yes, yes. Um, and I, you know, I wanted to transfer over some kind of older files from my desktop onto the cloud, but I was concerned that some of them were tax documents that have my social security number. And I was like, is that safe to store things on a Google drive is that, you know, hackable. And I looked it up and it's not like nothing is impermeable, but they've put in a lot of security in place to make sure that it is not easily hackable. Um, but I still haven't uploaded that sensitive stuff.
Jeffrey: And here, here's kind of to make an argument for that. You could just think of it this way. Do you have a team of security agents protecting your computer?
Katie: Um, besides the fairies that live in my office, I do not.
Jeffrey: Does Google have a team of security agents protecting their servers?
Katie: They ma they do. They do. In fact, they have the money for that. So, so let's talk about, you know, you mentioned there are all these types of attacks and attacks, and then you mentioned, you know, there's really a true cost to getting hacked and it's beyond the pain in the part of it, and right. It goes so much more beyond that. So talk a little bit about like what you've seen, um, of the being the true cost of being hacked. His, hopefully we're helping people find a password password management system not use the same password twice and start really taking this stuff seriously. So, yeah, what's the cost of that.
Jeffrey: So the costs, of course, the immediate cost that you think of is if you're, you know, if you're a soft system, whether it's your website or if you have a bigger, you know, server, whatever, you're a bigger business or whatever, usually, you know, we're small businesses, we're talking to small businesses. So it's, you know, usually your website, usually your website gets hacked and, um, you know, there's personal identity, identity identification stuff. There there's customer identification stuff. Maybe you're running a WooCommerce or maybe you're connected to a payment gateway, all that kind of stuff. Um, you know, so, so cleaning up a hack that's expensive, you can easily spend several thousand dollars having a team, you know, search through all of your site files, all of your stuff and, and trying to identify locate and eradicate malicious code. So on one hand, it's just expensive. Just the technical aspect of getting it done and clean that's expensive. Yep. Also ransomware, what if somebody says, Hey, send me $350,000 or all of your data goes, bye, bye. How are you going to recover from that? That is a low enough to put a lot of people out of business, right? You pretty much just either walk away from your data and start all over again or pay it and go bankrupt. I don't know.
Katie: I would think too, you know, I don't know if anyone cares about my data or I know they don't it's that I care. And so how much am I willing to spend that? But what I was thinking more of, and this is probably just too much like CSI TV or law and order, but it, you know, that they find some sort of photo that you wouldn't want to get out there. You know, like that's, what's happening with the Hollywood stars, right? Whether they're just like intimate photos between their partners or whatever. And they're like, we're going to splash this all over the internet. So it's really the reputation cost as well, which is hard to recover, even if you don't live in Hollywood.
Jeffrey: And that that's so true. And it's reputation on a several levels, whether or not they're digging into your data and pulling out like a, you know, a secret document or a secret photo or an incriminating photo or whatever. Like you might have that. But even if you don't have that, um, your reputation has also garnished because that breach just happened in your business. Your customers data is now out there in the hands of hackers. And that, that trust is now broken between you and your clients and your customers that trust is now broken. So sometimes that's the hardest thing to recover from is to say, no, no, no, no, I'm clean now I'm clean. Now let's do business again. Please give me your personal information again. No, no, no, no, no, really, really. It won't happen again. Right. And everybody thinks, Oh, it'll never happen to me. So they think, Oh, if it happened to you, there's something wrong with you.
Katie: Yeah. Like we talked about, it's not that you were dumb it's that you were unlucky, right. Or that somebody really good got, you know, like, like again, we talk about market sophistication. This, you know, scheme is, is sophisticated. I remember when I first started coaching and collecting, um, uh, credit cards and saving them on file for people that were going to continue, you know, with me month after month. And, um, so we're talking like 2011 and I just didn't, I, I had heard of Stripe, but it was like, so beyond me and PayPal didn't offer that feature at that time of the recurring payments, if they did, I didn't know how to use it. So I would write it on a red form piece of paper and I would keep it in my desk drawer. And when I lived with people like with roommates, I was like, Ooh, that is not safe. So I got a filing cabinet and at least locked them away. But still you think about like, Oh, a lock on a filing cabinet. Yeah. Those are super safe.
Katie: It's like I went and bought it at the, at the hardware store for $8. Like, I'm sure that's not pickable, you know, so it's just, it's funny though, because I really did think of that, like that they're protecting me with their credit card and I want to assure them that it's safe, you know, and I, and, um, shredding it after. So I've always been very safe with people's information because it is, um, it is necessary. And when I used to do sales at live events and people would write on those, um, carbon copy reg forms, the white is for us, the yellows for you, the pink is for whoever, what are those calls in CRM, NCR forms. Yeah. Right. Um, and so, you know, we D we were doing that. Like I stopped working for that company, but, um, two years ago we were still doing that.
Katie: And people were at this place where they were like, I don't want to write my credit card on this carbon copy. So we made it an effort, you know, every single time when we closed a sale and they signed it, we would have to turn it over face down just to show them like, your information is protected behind the table, like with us. And then any time a client tried to come behind the table, we wouldn't let them. And they thought, what's the big deal. We're all friends. But the whole big deal was that we were keeping people's information safe and we wanted them to have that trust in us. Right. So it's like, yeah, we're all friends, but still, we're not, you know, we have a lot of credit card information back here. And, you know, we're talking about, you know, when I worked for that company, I sold over $4 million of coaching packages.
Katie: There's a lot of credit cards, you know, at 15 to 20,000 each. Right. So, um, so anyway, it's, it's very true that if you haven't been thinking about that, how important it is, and really the online payment gateway systems make that easier now, more than ever before the burden is now off of us and in the hands of the online space. And then it's your job to keep your password very safe. Um, but, and I, but the way I understand it too, is that even if someone logged into my Stripe account, um, I can't see someone's complete credit card number it, so they keep it safe too. Right. But it's still like that double, double lock, I would assume. But
Jeffrey: Yeah. And here's just a touch on that a little bit. That's kind of a, really a real benefit to using a good payment gateway is that the PCI compliance is off of you. Like if you're doing transactions and you're, Oh gosh, uh,
Katie: Should I Google it real quick? Anyway, keep going. You were saying the PCI compliance comes off of us and onto the payment gateway system.
Jeffrey: Exactly. And if you're doing online transactions, you're not storing anybody's personal information or at least credit card information, uh, you know, and that payment gateway is taking on that responsibility, keeping up with their securities, um, assessments doing the PCI audits, if you will. Um, you know, cause there is a lot of responsibility when we think of like, you know, why is there a convenience charge for using a credit card? Um, uh, Oh, right. PA PCI payment card industry data security standards. Yeah. Payment card industry. All right. Katie just looked that up by the way,
Katie: Who knew there was an industry, you know, it makes sense, but who knew not me.
Jeffrey: Right. And that's why there's a convenience charge. Right? Those companies need to stay in compliance. They need to rigorously check their security. They've got entire teams and segments of their company dedicated to it. So, you know, every time we swipe our card, there's a little charge for that. And that's the convenience and it's the it's for them to keep within compliance. And thankfully we have a compliance system that says that's looking out for our best interest.
Katie: Yep. Oh my gosh. Thank you so much for saying that. I think, um, it's really, you know, business owners. We, we're always looking at the bottom line, you know, we're always saying like, why would I pay for a password production system? If I have a trusty notebook I've been using since 2002, right. Or, you know, those darn credit card companies charging me a fee, how dare they charge me money to collect money from my client. And then miraculously put it in my bank account that should be free. Right. It's like everything costs money. Yeah, exactly. It's like, you can't do that. And it's just like, it takes money to make money. And you know, the people that are always trying to get around those fees or using, you know, um, and I think this is the biggest one, choosing a payment processor that is not meant for business because the securities are not in place.
Katie: And when you're a business owner and you're choosing to skirt the fees and use those companies instead you are not putting your companies or your client's information in a safe place, um, for business. Yeah. And you know, I feel like, so I'm just glad you said that. It's just, you know, I obviously we're, we looked at the same thing, you know, geez. When you sell a $30,000 product, those fees are high, right? Like that dollar amount is high, but at the same, it's just, I feel like it's insurance and it's insurance for both parties. It makes people feel safe. You know, it is what it is. It's the cost of doing business. I've never been the person to pass that fee onto my customer. I think that makes you look like you're penny pinching. And when you're selling a $30,000 product, you're not going to be like, there's an additional fee of $650. Yeah. That just doesn't, that doesn't make sense. So, um, I know, so it depends on your price point and things, but no, it's important that we're paying for that security and to understand that. So, um, yeah. Well, any final words as we're wrapping up our, our hacker talk.
Jeffrey: Yeah. You know, I think really what I want people to take away from this is that a password manager should be mandatory for your business. Just, just think about it. And if you're sitting out there like, Oh, I don't want to learn something new. Oh my God, just one more software to do it, do it. This should be mandatory for all business owners. If you care about your reputation, online, your reputation with your customers, the trust that they provide in you, if you care about that at all, a password manager should be mandatory.
Katie: And I think you put in that word insurance, if you pay for health insurance, business insurance liability insurance, a password system is insurance.
Jeffrey: Yes. It's insurance. That's so true. Like we buy homeowners, home insurance, business insurance, car insurance, renter's insurance, right. This is, this is security insurance. Yeah.
Katie: Yep. And it's so cheap. It like when I signed up for it, it was $3 a month. It's ridiculous. It's so cheap.
Jeffrey: And there's like a whole slew of benefits. We don't need to get into them, but how easy is it to now fill in a password when you've got it in there? How easy is it to save a password when it's in there? How easy is it to update a password when it's like, it's like, once you learn that system and you just get over that little learning curve hump, which is minuscule, by the way, like there's all these other, other benefits that just make working online and doing business online so much easier. So,
Katie: Yup. All right. Quick story. Before we wrap up. So when I did make the move from my trusty notebook to last pass, because you did a live on this in our Facebook group. So for the listeners, if you're not already in there, go ahead and join, lighten your launch Facebook group. And so Jeffrey did a live in there and we got an email, we've got a couple of comments on that live. And we got a special email from someone that was saying, thank you so much for talking about this password protection. And she said her, her, um, obstacle was simply the time it was going to take her to enter in all those passwords. So my quick story is I finally decided, okay, I'm going to do this. It, it just, it was, it was something I had to put on my calendar and set aside about an hour to, to really do it all and go to all the sites and whatnot. Anyway, I, so I spent probably over an hour, got them all in there and I got to pick my master password and they recommended that you pick a strong password and copy and paste it somewhere. So I'm like, well, okay, I'll do that. So I did the strong password and I forgot the step of copying it. And they're so secure that if you don't have your master password, you have to delete and start all over again. Yeah. And I,
Jeffrey: Yeah, these companies don't even know your passwords. These companies are, have security in mind. No one at the company knows your passwords can see your passwords at all. Yeah.
Katie: Yeah. So I remember, I think I even called or tried to do a chat. Like there's gotta be a backdoor. There's gotta be, you know, I just spent a whole hour and you know, me, I don't have time as something like that all the time. It's my racket, you know? And, um, and so anyway, if that happened to a lot of people, they would have gotten up and been like, forget it. I'm going to keep with my trusty old notebook. Right. But I knew, Nope, this is so important. I have to spend the next hour doing it again, doing it better, understanding the system, picking a master password that I will not forget, but is not random that I don't have to copy and paste. And you know, so anyway, it's like, make it important set aside time in your calendar. For me, it was a Sunday. It was just one of those things that I thought I've got the time to do this. It's a chore, just like laundry vacuuming. I have to take care of this password thing. So we just can't stress that enough. If that's your one takeaway for today, look at either last pass or one password highly recommended.
Jeffrey: And I'll say that, I'll say that one password is thought or one password has thought about this. And when you sign up for an account there, they, they create a PDF. That's got a special, like literally a 26 digit character thing that you can print out as a PDF, put it in a filing cabinet. And if you forget your master password, you can use this special code one time to get back in.
Katie: See how he's one-upping my last pass.
Jeffrey: I am an advocate of one password I am.
Katie: Yeah. Yeah. Either way something better than a notebook, sticky notes or your memory is the way to go. Yep.
Jeffrey: Oh, and one more thing. One more thing. I just thought of that when we're going back to the fishing and fishing and whaling and smishing and all of those kinds of things, really the bottom line to this is never, never click a link in your email unless you know who the person sent and you can validate their email. And you were that link. If it's Facebook saying there's been a strange log-in, you need to click here and check it out. If it's your bank saying, Hey, somebody just logged into your thing or changed your password to change it back, click here. If it's anything like that, don't click it. Don't click the link in your email, just open a web browser, go to that website and log in. Yep. Because that link, the whole point of the fishing is to spoof where you land. So it looks exactly like your bank. It looks exactly like WordPress Facebook. Yup. It looks the same. It will be undetectable unless you're looking at the code it was built on and most people don't do that. Yeah. Maybe I'm just weird, but I do.
Katie: We love you for your tech geekness Jeffrey, the tech nerd in you is just appreciated. Yeah.
Jeffrey: I just, I just had to get that message in there. Just don't click just yet.
Katie: Yeah. Don't click it. Um, awesome. Well, thank you so much for joining us. If you enjoyed this episode, please leave us a five star review. They are super helpful for us and hit the subscribe button. You can check out the show notes at the launch squad, lab.com forward slash episode. Number 12. Thanks guys.
Announcer: Hey, thanks for listening. If you'd like to have clarity, confidence and excitement around your next launch, join us in the Lighten Your Launch Facebook group today at thelaunchsquadlab.com/facebook. We also invite you to download our free gift, the Lighten Your Launch starter kit, the free guide to creating an irresistible offer, pricing it right, overcoming tech barriers, and tapping into the energy you need for success. Get it now at thelaunchsquadlab.com/freegift. [inaudible].
Be the first to know
Enter your name and email and we'll let you know when new episodes release.
About the Show
The Lighten Your Launch Podcast is for Coaches and Course Creators who want a lighter online launch experience. Maybe you’ve done a few launches already, and feel exhausted just thinking about it! Or, it’s been one of your goals, but you don’t know where to start.
Tune in to learn from our team of experts, The Launch Squad, who aren’t afraid to dig into all aspects of launching: sales, strategy, technology, mindset, funnels, and even a bit of woo to get you through the toughest times. Let’s put a stop to perfectionism and procrastination, and finally take your launch from intimidating to money-making!









![Marketing Launch Calendar [TEMPLATE]](https://thelaunchsquadlab.com/wp-content/uploads/2023/05/Marketing-Launch-Calendar-TEMPLATE-300x260.png)


![[Updated] Email Templates for Launch](https://thelaunchsquadlab.com/wp-content/uploads/2023/05/Updated-Email-Templates-for-Launch-223x300.png)
![[REVISED] LS Pitch Script](https://thelaunchsquadlab.com/wp-content/uploads/2023/05/REVISED-LS-Pitch-Script-2023-226x300.png)